Securing your Bitwarden and LastPass Vaults
Recently, LastPass reported that an attacker was “able to copy a backup of customer vault data from the encrypted storage”. For LastPass users, this means that an attacker could have a copy of “unencrypted data, such as website URLs, as well as fully-encrypted sensitive fields such as website usernames and passwords, secure notes, and form-filled data.”
Because sensitive data is encrypted, this attacker may not be able to access it, at least not immediately, but given they have all the time in the world to try, it’s possible they’ll eventually crack the encryption and gain access to the passwords contained within.
There are at least two factors that can make it harder to crack your encrypted data:
- The strength of your master password
- The number of iterations of hashing used on your vault
The purpose of this article is to elaborate on (2). If you have an existing LastPass account, I’d advise you to
- Change your master password for LastPass (and anywhere else that uses that same password)
- Update the number of hashing iterations used on your vault
- Start changing the passwords for the accounts stored in your LastPass vault, in order of most sensitive/import to least sensitive/important
Unlike LastPass, Bitwarden don’t seem to have a help page describing how to increase the password hashing iterations your vault uses, so I’m going to document this for Bitwarden here.
Firstly, though, what are these password hashing iterations?
In simple terms, when you set a master password for LastPass, Bitwarden, 1Password, or some other password managers, that password isn’t used on its own. Some complicated math is performed on your password to generate a new password-like thing (called a hash), and this is done thousands of times. The beauty of this process is that it’s one-way (you can’t find the password from its hash), and it is slow. Converting the password to the hash takes a computer a bit of time, and doing it thousands of times just increases that time. This means that anybody trying to guess your master password also has to go through this slow process of generating this hash thousands of times, for each password guess they make. The idea is that it’ll take so long to crack your master password this way that it’s just not worthwhile.
By default, Bitwarden, LastPass, and 1Password all have about 100,000 iterations of password hashing set up on your vault, which isn’t too bad. It’s worth noting that older LastPassword accounts, for example, might have a lower number of iterations, and therefore be easier to crack.
According to OWASP (“a nonprofit foundation that works to improve the security of software”), the recommended number of iterations for PBKDF2-HMAC-SHA256, the hashing algorithm used by 1Password, LastPass, and Bitwarden, is 310,000.
Setting your KDF iterations with BitWarden
LastPass document how to change your password iterations on their website.
Here’s how to do the same for Bitwarden:
NOTE: This will log you out of Bitwarden on all of your devices, and you’ll need to log back in afterwards.
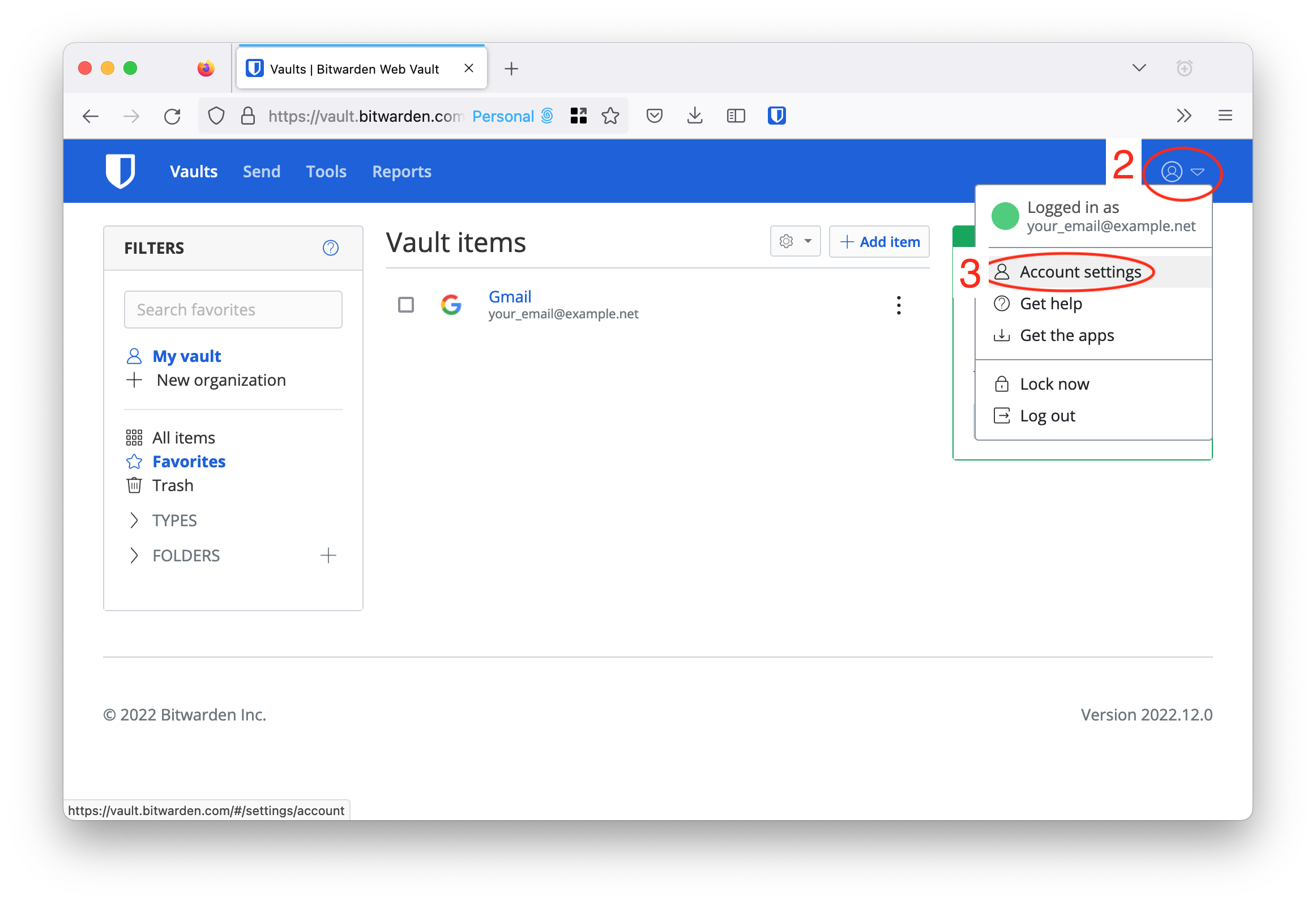
- Using a desktop web browser, log into the Bitwarden web vault (the web page, not the browser extension) at vault DOT bitwarden DOT com (I’ve not made this a link because clicking links to get to your password manager is a recipe for getting phished; just type it into the address bar, it’s not that hard)
- In the top-right, select the little down-arrow beside the outline of the person in the circle
- On the menu that pops up, select “Account settings”
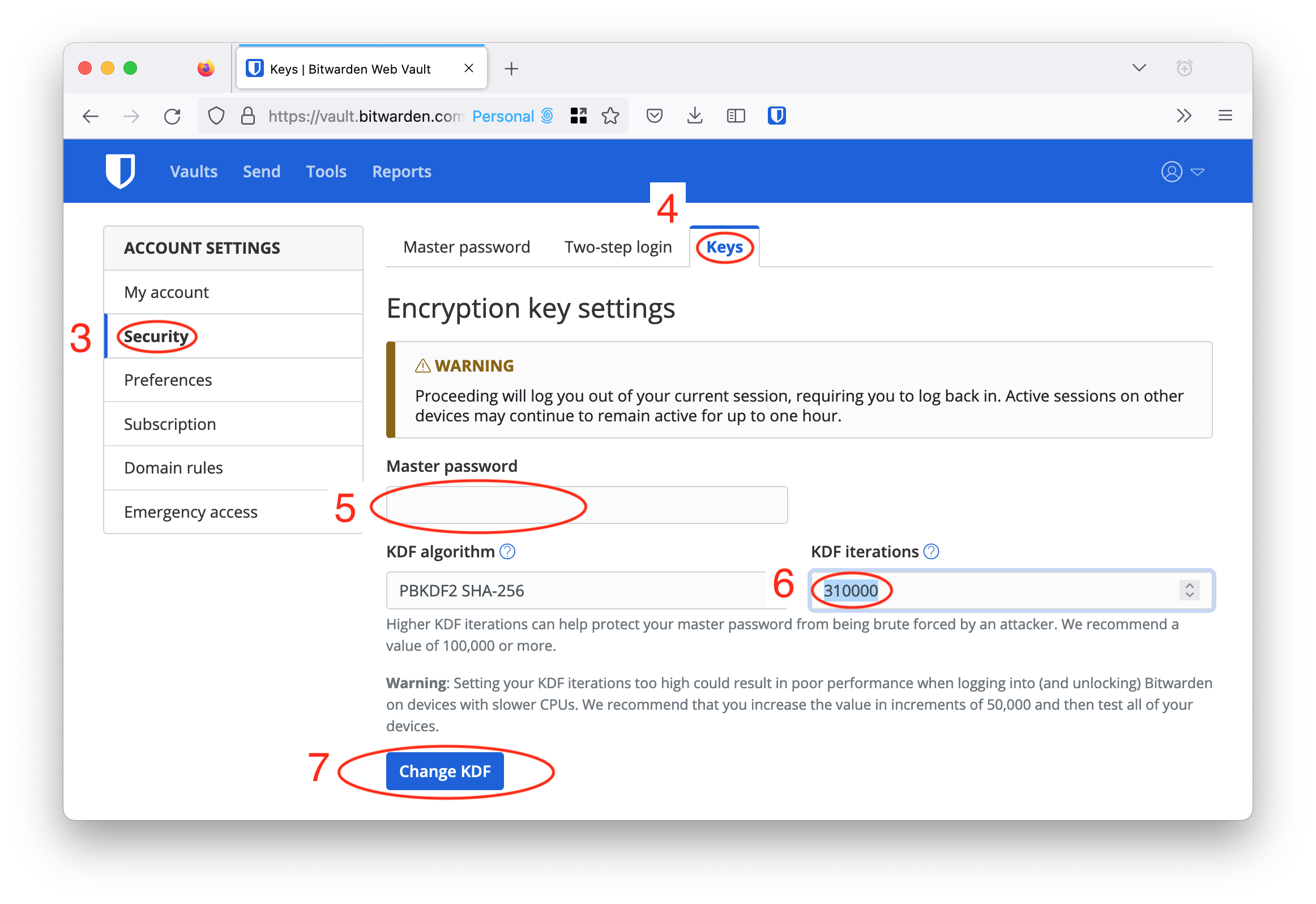
- On the left-hand menu, select “Security”
- Select the “Keys” tab on the top of the page
- Enter in your master password
- Set the “KDF iterations” field to 310,000
- Select “Change KDF”
- Log back into Bitwarden on all of your devices
This should ensure your password vault is sufficiently secure for now, even if someone does get access to an encrypted copy of it.